What are you looking for?
- Samsung Community
- :
- Products
- :
- Computers & IT
- :
- Re: Samsung SSD 970 EVO Plus drive encryption won't change from Ready to Enable
Samsung SSD 970 EVO Plus drive encryption won't change from Ready to Enable
- Subscribe to RSS Feed
- Mark topic as new
- Mark topic as read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Labels:
-
Memory & Storage
18-10-2019 09:00 AM - last edited 18-10-2019 09:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Highlight
- Report Inappropriate Content
I am setting up a brand new machine with the above drive and have installed a discrete TPM 2.0 header on the motherboard to allow me to use hardware encryption with BitLocker. Windows 10 Pro x64 1903 is in use.
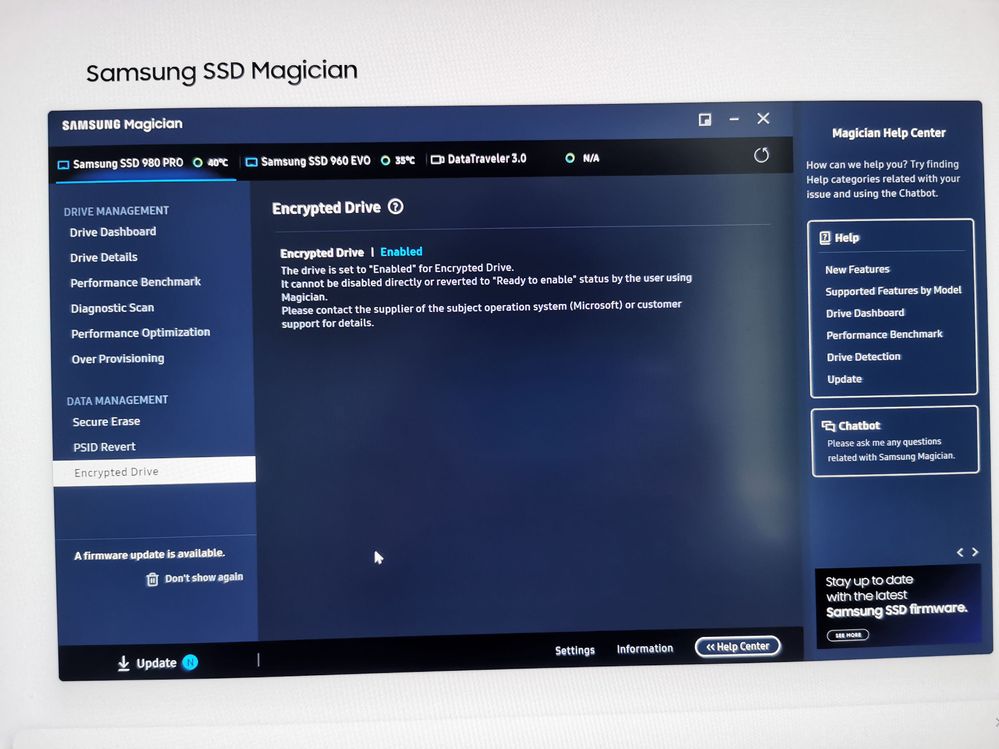
I installed Windows and Samsung Magician 6.0 and switched on drive encryption within the Encrypted Drive part of the tool. It shows "Ready to Enable" as a status. I create the Secure Erase tool, but the tool cannot find the drive. Going back into Windows I updated the drive's firmware to 2B2QEXM7. I reboot and run Secure Erase. The drive is successfully detected and the tool reports that it completed successfully. On rebooting the computer cannot detect bootable media, indicating success.
I disable Legacy USB and CSM support in UEFI, then boot my Windows 10 USB installer. The drive is showing as empty, no partitions. I create a single disk partition (with Windows creating its standard recovery partitions) and finish the install.
After booting into Windows I install Samsung Magician, but Encrypted Drive is still reporting the drive as "Ready to Enable" rather than "Enabled". I try repeating the Secure Erase and installing Windows process, but the status is still "Ready to Enable".
I've done this previously (on a different computer) with a Samsung SS 840 EVO, but did not encounter this problem. At this point I am not sure what more I can do. It would seem that Secure Erase is not flipping whatever switch it is supposed to, but it's not reporting any errors and is erasing the drive. The Windows 10 install is on a completely fresh drive.
- « Previous
-
- 1
- 2
- Next »
09-08-2022 12:44 PM - last edited 09-08-2022 01:14 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Highlight
- Report Inappropriate Content
After countless hours of testing and trying I will post the steps I took for a specific configuration, maybe it will help others.
Motherboard: ROG STRIX Z690-I GAMING WIFI Bios version: 1601
SSD: Samsung 980 Pro NVME Firmware version: 5B2QGXA7
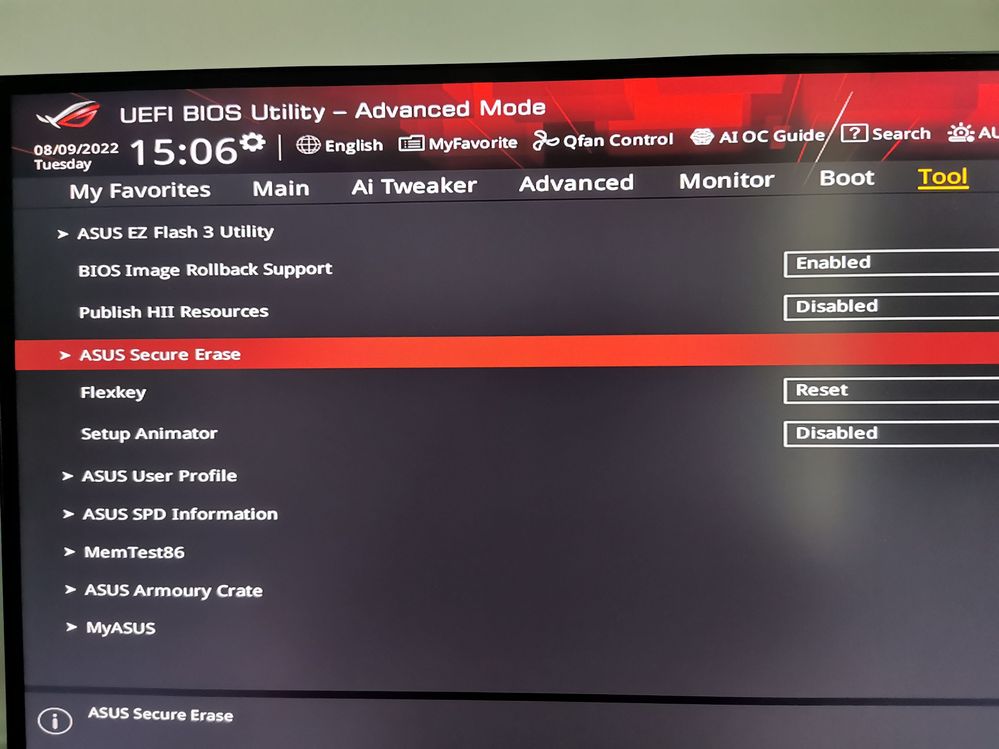
Because the USB stick created with Magician (version 7.1.1) doesn't boot I have performed a Secure Erase using the motherboard BIOS Option (Tools -> Asus Secure Erase).
NOTE (as I have documented): Secure Erasing put the drive in factory state and generate a new DEK (encryption key) used to encrypt data on the drive. So, if you don't intend to generate a new key (and especially in the case of new drives) I don't think it is absolutely necessary to do a Secure Erase of the drive. (maybe someone with a new drive can confirm this).
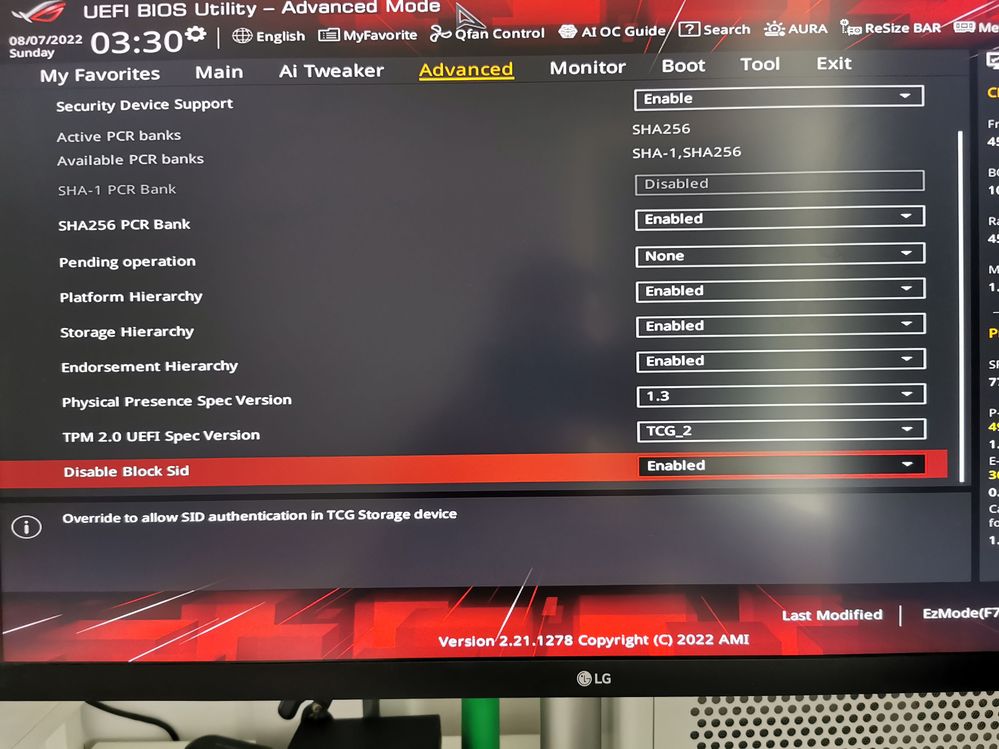
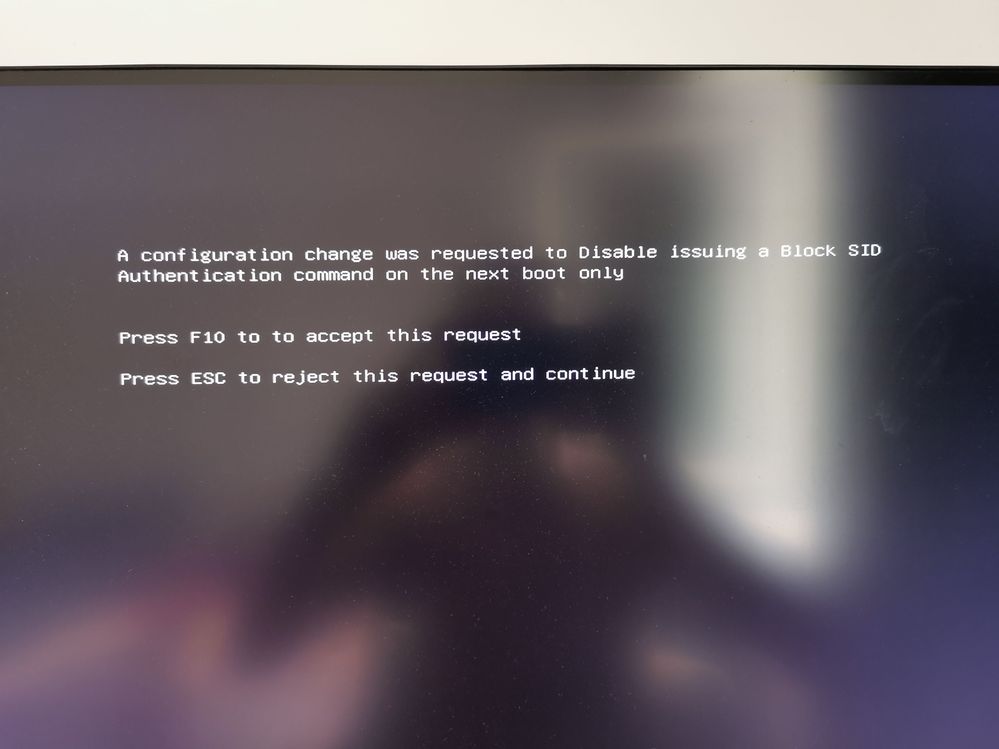
To Enable "Encrypted Drive", I had to temporary disable "Block SID". On my board it can be disabled only "for one boot" (meaning that after reboot the setting will toggle again to enabled), but it was enough.
Also note that on my BIOS the Option name is "Disable Block Sid" which means that in order to deactivate it, it must be set to the Enable state.
After Disabling Block SID I was presented with this screen:
After that I have booted the Windows 11 installation media (Windows 11 bootable USB stick) and installed Windows 11.
After installation:
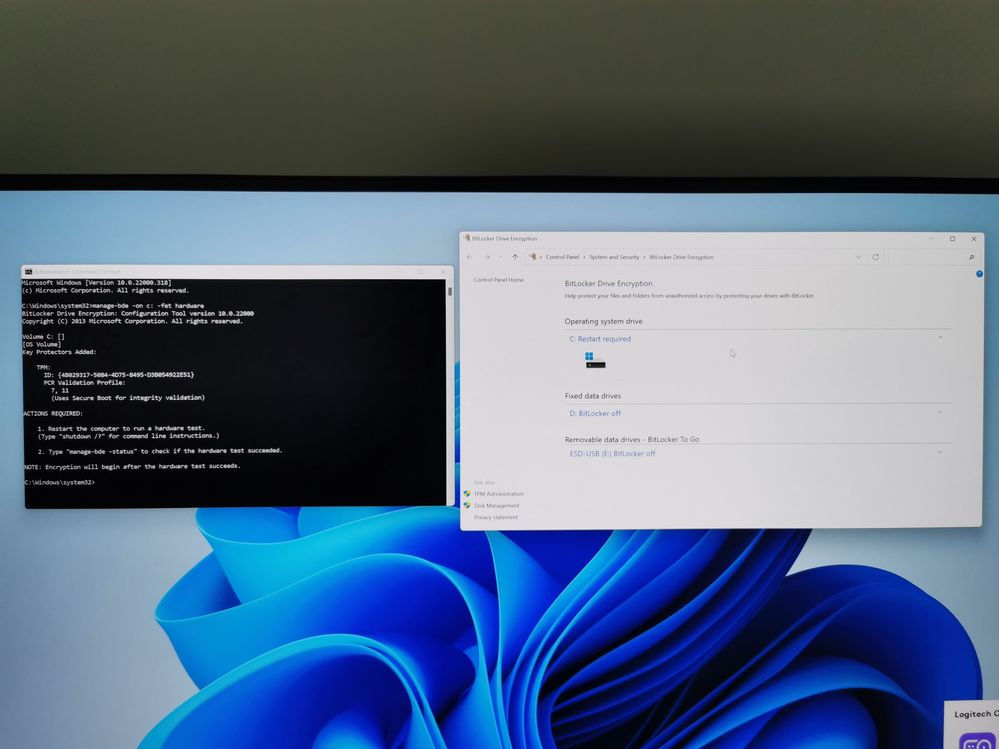
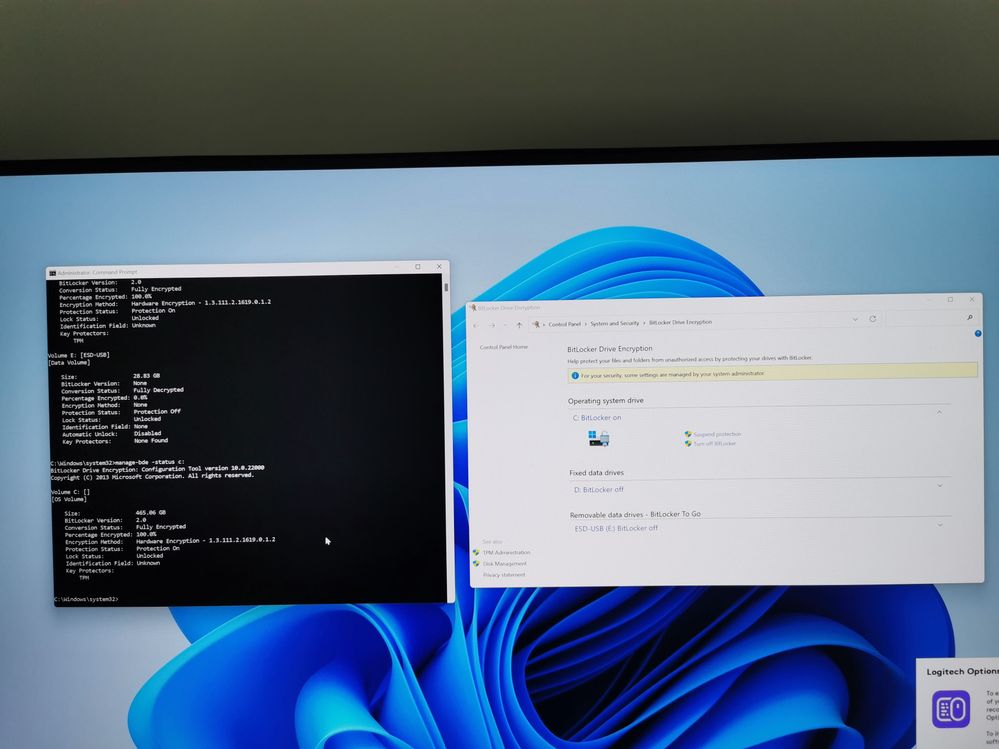
So, in order to hardware encrypt your volume you need to use the BitLocker command-line tool (manage-bde) : manage-bde –on C: -fet Hardware
After computer restart:
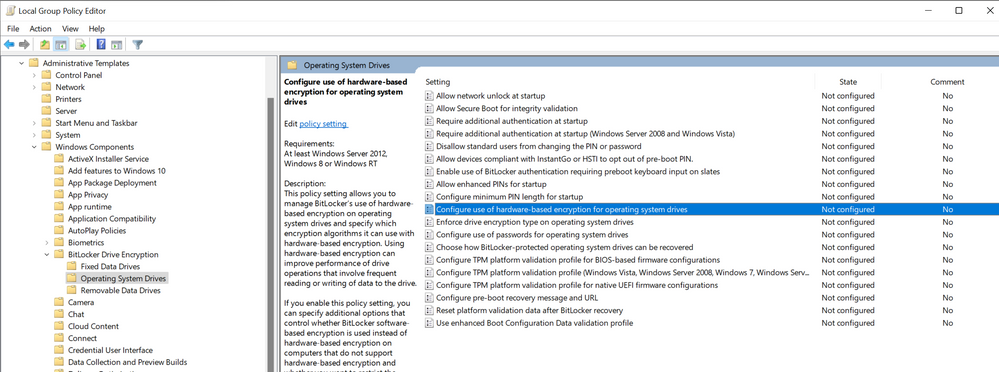
If you want that BitLocker use by default hardware SED encryption then you need to use BitLocker group policy settings.
For example, for hardware encryption of the Operating System Drives (my case) you need to Enable "Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives"
12-03-2023 08:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Highlight
- Report Inappropriate Content
Samsung Secure Erase CERTAINLY DOES BOOT, but not in UEFI mode. You need to go to the BIOS Boot screen and enable CSM (Compatibility Support Module). In the Secure Boot screen, you need to specify "Other OS" (not "Windows UEFI Mode"). After running Secure Erase, you'll need to change these settings back in order to boot Windows.
14-08-2023 11:37 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Highlight
- Report Inappropriate Content
Greetings!
I tried to follow your tutorial, but now i am stuck in powershell(as administrator)..
I want to use Bitlocker with hardware encryption on ssd m2 970 evo plus 1tb and I will install windows 10 pro on that 970 evo plus
Here is some system information:
OS Name Microsoft Windows 7 Ultimate x64
Version 6.1.7601 Service Pack 1 Build 7601
BIOS Version/Date American Megatrends Inc. 3805, 16.05.2018
Motherboard Z170 Pro gaming (with last bios update and last Intel ME update)
My problems..
1.How to disable "block sid"?
2.I heard that i need to disable "Legacy mode" - The computer must always boot natively from UEFI. If i disable (CSM) that mean the computer will run only on UEFI? CSM = legacy mode? i am not sure.
3.I want to use only a password for bitlocker, i mean i don't want the ssd to work only on my motherboard(i want to put it in other pc's). I think that mean i don't have to use tpm? is that possible? Thanks!
21-08-2023 08:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Highlight
- Report Inappropriate Content
Hi,
Powershell version must be OK. Othervise i would expect error to be something like "does not contain a method SetPhysicalPresenceRequest" or "Class not exist". Maybe try to clear TPM from a bios and try again. If same error - then most likely Your MB/UEFI refuses to config this stuff via powershell.
Reg. legacy mode/CSM/UEFI -- from my experience at the end You need CSM=disabled / Legacy mode=disabled. Not sure though if You won't run into issues with this because of Windows 7. Not what i didn't like Windows 7, i did a lot beleive me. But it is like few years EOL, so good oportunity to update. Maybe it even would let You succeed with $tpm.SetPhysicalPresenceRequest(97) ..
Yes, You can do bitlocker without TPM, with password input on boot. You need to change option via gpedit.msc. Google - "GPO Bitlocker without TPM" - for instructions. Although, even if You go with TPM You will also receive long recovery string upon enabling. You can use that string to unlock drive on another pc. Or on the same pc if it's TPM get's cleared or breaks, or You make some big changes to hardware in Your PC. Just be cautious that it will not always work with Hardware Encryption, because that "other pc" might not be compatible with it. For example, if i pull out one of SATA3 Hardware Encrypted disks and try to connect it to other PC (or even to the same) via SATA-to-USB adapter - it won't ever work. Cause HW encryption requires SATA with AHCI mode, native MS drivers etc, etc. So in scenarious where You need to frequently move bitlocker-encrypted drive around PCs without much headache i would suggest using software encryption.
- « Previous
-
- 1
- 2
- Next »
-
Cellular missing on Book 3 pro 360 with Giff Gaff Sim fitted
in Computers & IT -
SSD 990 PRO: BitLocker encryption not working
in Computers & IT -
Issues with the Samsung Odyssey G9 Neo and What I’ve tried to solve it!
in Computers & IT -
RAPID Mode on 850 EVO SSD problem
in Computers & IT -
Odyssey Neo G9 - connecting two devices (is a pain)
in Computers & IT